Documentation
Agent
Havoc default agent which is called the Demon agent has a lot of builtin features and it's malleable and modular by design.
About Evasion
You might ask if the Demon agent bypasses anti-virus (AV) products or even endpoint detection and response (EDR) products, most likely not. The Demon agent wasn't designed to be evasive nor was it within the scope. It was designed to be as malleable and modular as possible to give the operator as much power over it to adapt it for the red team operation without overloading it with evasion techniques and features that are going to be most likely burned and going to be an IOC by itself. And the devs of the agent don't wanna play the cat and mouse game with AV & EDR vendors. That said, the Demon agent is designed to be interoperable with common techniques for bypassing anti-virus software such as loaders, packers, crypters, and stagers.
Demon Features & Configuration
The Demon agent has a lot of features that can be used and configured.
In the payload generation window (Attack -> Payload) you can configure your Demon payload.
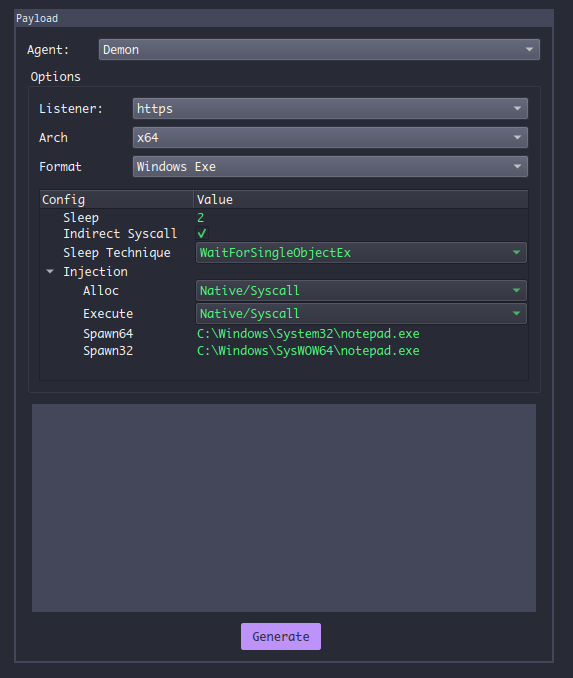
| Configuaration | Description |
|---|---|
| Sleep | Sleep delay between each callback |
| Indirect Syscall | Use of indirect syscalls |
| Sleep Technique | Sleep obfuscation technique. |
For the sleep obfuscation technique, 3 options can be used.
Foliageis a sleep obfuscation technique that creates a new thread and usesNtApcQueueThreadto queue an ROP chain that encrypts our agent memory and delays execution. (Author of this technique is Austin Hudson)Ekkois a sleep obfuscation technique that usesRtlCreateTimerto queue up an ROP chain that encrypts our agent memory and delays execution. (Original Github repository)WaitForSingleObjectExis not a sleep obfuscation technique. It just delays the execution and doesn't perform any kind of sleep encryption.
Injection Configuration:
| Configuaration | Description |
|---|---|
| Alloc | What technique to use when allocating memory. |
| Execute | What technique to use when executing a pointer. |
| Spawn64 | x64 injection target for post exploitation modules |
| Spawn86 | x86 injection target for post exploitation modules |
Native/Syscall is using NtAllocateVirtualMemory/NtCreateThreadEx either from Ntdll.dll or if Indirect Syscall has been checked it's going to build a stub that uses the syscall instruction from another native function (which in this case is NtAddBootEntry).
Win32 is normal windows API (VirtualAllocEx/CreateRemoteThread)
Demon Commands
The following commands are available to the.
| Command | Type | Description |
|---|---|---|
| help | Command | Shows help message of specified command |
| sleep | Command | sets the delay to sleep |
| checkin | Command | request a checkin request |
| job | Module | job manager |
| task | Module | task manager |
| proc | Module | process enumeration and management |
| transfer | Command | download transfer module |
| dir | Command | list specified directory |
| download | Command | downloads a specified file |
| upload | Command | uploads a specified file |
| cd | Command | change to specified directory |
| cp | Command | copy file from one location to another |
| remove | Command | remove file or directory |
| mkdir | Command | create new directory |
| pwd | Command | get current directory |
| cat | Command | display content of the specified file |
| screenshot | Command | takes a screenshot |
| shell | Command | executes cmd.exe commands and gets the output |
| powershell | Command | executes powershell.exe commands and gets the output |
| inline-execute | Command | executes an object file |
| shellcode | Module | shellcode injection techniques |
| dll | Module | dll spawn and injection modules |
| exit | Command | cleanup and exit |
| token | Module | token manipulation and impersonation |
| dotnet | Module | execute and manage dotnet assemblies |
| net | Module | network and host enumeration module |
| config | Module | configure the behaviour of the demon session |
| pivot | Module | pivoting module |
| rportfwd | Module | reverse port forwarding |
| socks | Module | socks4a proxy |
The help command
Shows how to use the specified command.
| Expected Arguments | <command> |
If a parameter is around a
[]then it means it is required to specify the argument.If a parameter is around a
()then it means it is optional and can be left out.
The sleep command
Sets the sleep delay between each tasking routine and request. The delay should be specified in seconds.
| Expected Arguments | <delay> |
The checkin command
Requests a checkin request and displays the metadata from the checkin request.
Still under work
This section is in work. It will be published soon.

On this page
- Agent
- About Evasion
- Demon Features & Configuration
- Demon Commands
- The help command
- The sleep command
- The checkin command
- Still under work